5 Ways Veeam Provides Ransomware Protection
- Brad Linch
- Apr 6, 2020
- 6 min read
Updated: Aug 23, 2021
A simple google search will yield tons of statistics on the cost of ransomware, and how many companies have fallen victim to its attacks. The numbers vary so greatly that I'm not going to cite any particular source, but it is clear that ransomware is real, not going anywhere and can cost your business a significant amount of time and money.
What is Ransomware?
First, let's start with a high-level overview on what ransomware is and how it works. Ransomware most commonly sneaks in via email attachments or links, but it can also come from clicking or downloading a link from a malicious website. Once the infection has been downloaded to its new home it begins to spread. It starts by installing a program on the local machine it gained access to and ensures the program starts on reboot. From there ransomware will look to spread across the network to gain access to as many endpoints as possible. Once it has achieved that it will begin to search for files with important extensions such as .doc, .xlsx, ppt, etc and encrypt them, so they are unusable. More sophisticated attackers will wait until you're infected for 30 days or more before demanding payment because at that point you may have fallen out of your retention policy. Your backups would now be useless, since you've been protecting encrypted files. Spoiler alert: later we will cover how Veeam can detect this behavior!

How to defend against Ransomware?
As part of your ransomware strategy your first line of defense should be yourself! Similar to a cold or flu, ransomware is an infection. If you never wash your hands, constantly eat finger-foods, and always touch your face, then your chances of infection are significantly greater! The same is true for ransomware. If you don't take proper precautions by using strong passwords, applying software patches, and limiting/restricting access to endpoints on the network, then you're putting yourself at greater risk. Your second line of defense are tools and vendors that offer solutions specifically to fight ransomware! Think of these as your yearly flu shots. They aren't guaranteed to keep illness away, but they are usually effective. They will scan the network for suspicious activity, analyze emails for phishing content, prevent suspicious downloads and much more. Your final line of defense should be a backup solution that can save the day if needed and has ransomware built-in to the heart of the product. Just like the flu there is no cure you can take, but with proper fluids and medicine you'll be back to normal in no time! With that, let's cover the 5 ways Veeam can help.
5 ways Veeam can help:
1. Alarm notification if backup file size growth is abnormal! Despite the spoiler above this is a great defensive strategy to have in a backup solution. The best way not to pay attackers their ransom is to simply restore from a backup, but if it's a smart attacker who waited days or even weeks to demand payment then you might not have a valid backup. Veeam provides an alarm that can notify you if backup file size growth is abnormal, moreover, Veeam can take automatic remediation via a provided script to turn off the VM or remove it from the network. The reason this alarm can be helpful is because if an attacker is encrypting all your files than the backup sizes should be significantly larger since there are more changed files and less files that can be compressed and deduplicated. This is a great indicator to check if these VMs have encrypted files on them.

In the alarm, you can define rules for what abnormal file size growth looks like. For example, below we've specified Veeam to look for any backup files that exceed 150% growth, and we've instructed Veeam to compare the file to the previous 3 backup files in the "analysis depth" field.

You can setup Veeam to simply send you an alarm notification when it gets to the warning (150% growth) or error (200% growth) stage, or you can have Veeam take automatic remediation actions. In the actions tab, you can insert a script that will run if the above rule is meant. A common script might be to shut off the VM or remove it from the network. As you can see in the "execution type" field you can choose to receive an email first to approve the execution of the script.

2. Scan for possible malware activity. A second capability Veeam provides as a layer of protection against ransomware is an alarm that looks for high cpu usage or a high write rate on the underlying datastore.

Similar to the previous alarm you can set rules to look for high cpu usage, high write rates, latency on the datastore, network transmission rate, and many other variables. High CPU usage is a great indicator that files on the VM are being encrypted as that is a CPU intensive task. Now, it might be common in your environment to have VMs with high CPU usage. In that case, leaving it as an alarm notification with no automatic remediation might be best. In addition, you can suppress the alarm during snapshot deletion or creation activities.

3. Immutable backups offsite. Offsite backups in and of itself is a great strategy against ransomware. This gets a copy offsite and to a separate network. In some situations this isn't enough though. Veeam offers a capability with AWS to make secondary copies of data immutable. This functionality will extend to other public cloud and on-premises vendors in the future, but there was no reason to let this capability with AWS sit idle. When adding an AWS S3 bucket to the Veeam console, you can choose to select the number of days you want backups to be immutable. For this period of time nobody can modify or delete the backup. Not a Veeam admin user. Not a root AWS user. It locks the objects in what AWS calls compliance mode. Not even a support call can lead to deletion of this data. As a side note, I really like that there is an option to limit storage consumption if you know the business shouldn't exceed a certain amount of TBs or PBs.

As expected, if we try and delete objects in the AWS bucket as a root user it gives us an access denied because the object is locked for 7 days.
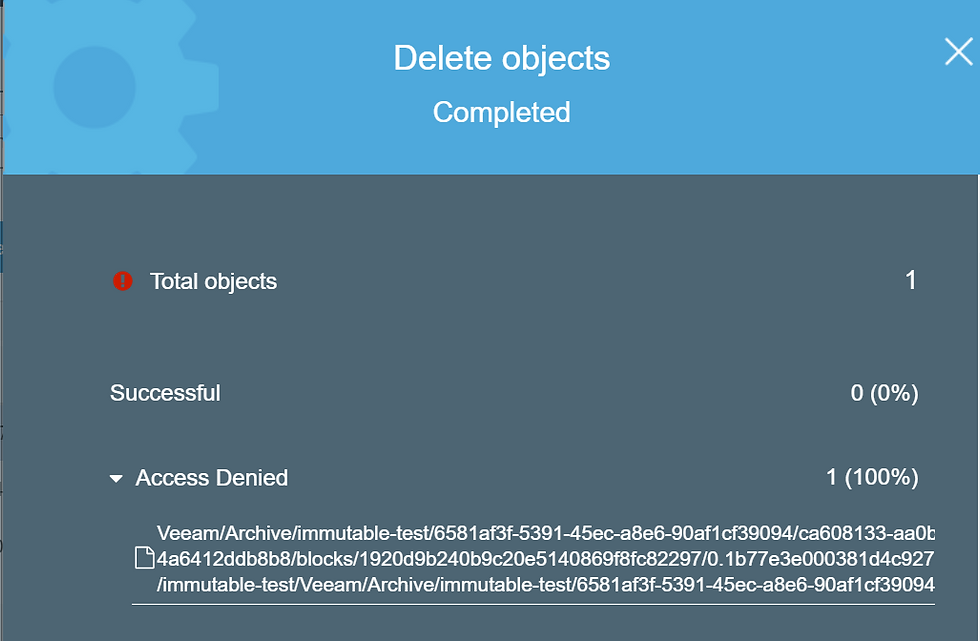
And if we try to delete the backup files in Veeam as an admin account it also fails because the objects are locked.

4. Automatically test backups in an isolated environment for ransomware or malware. Veeam SureBackup and SureReplica have been in the product for years. This is a powerful capability that enables users to put their backups to work. Whether it is to automate DR tests, spin up RA environments for test/dev, security, DBAs, analytics, etc. The use-cases are countless. One of those use-cases though is to test your backups for malware or ransomware.
First, you create what I refer to as the plumbing. Veeam calls this a Virtual Lab though to be more official. This is where you define the host, datastore, isolated network, and masquerade IP you want these VMs to spin-up in.

Once the plumbing is setup you can point VMs to the virtual lab and have automatic tests run once they are turned on. For example, you can check if a DNS port is open, a SQL database is online, guest tools is installed, or you can insert your own scripts to execute. In addition, you can have Veeam scan the files for any suspicious malware or ransomware. Not only can you do this in an isolated lab, but also when you do any type of restore back to production. Before restoring the data Veeam will mount the backup and scan it for viruses. If anything is found it will abort the recovery.

As you can see, this quickly becomes an option to take annual DR testing to the next level. I've seen customers who run this on a daily basis after their backups. I understand that might not work for customers with thousands of VMs, but why not make what used to be a yearly DR operational restore or backup validity test and turn it into a quarterly test?

5. API to mount any virtual disk to any machine for ransomware or malware testing. Veeam offers a Data Integration API that enables users to easily re-use and access their backup data for a number of use-cases. Scanning for viruses being one of them. Here is how it works!
$backup = Get-VBRBackup -Name "Name_of_Backup_Job"
$targetServerName = “192.18.138.125”
$targetAdminCredentials = Get-VBRCredentials -name "DEMO\Administrator"
$restorepoint = Get-VBRRestorePoint -Backup $backup | Sort-Object –Property CreationTime | Select -Last 1
$session = Publish-VBRBackupContent -RestorePoint $restorepoint -TargetServerName $targetServerName -TargetServerCredentials $targetAdminCredentials Ransomware is prevalent and any company that doesn't have or is not forming a ransomware strategy to prevent, detect, and recover from a ransomware attack is at a significantly higher risk of infection. As a first line of defense, do what you can to harden your infrastructure. That includes Veeam as well. If I can only recommend one thing it is to enable 2FA on all Veeam login server sessions. See this post from Rhys Hammond for a how-to. Second, find tools or vendors that can help with prevention and detection. Lastly, choose a backup software that has ransomware protection built-in to the product.
God Speed!

Comments